 A content delivery networks provide rapid content delivery across a large geographical area. Using a CDN for images and videos will significant improve page loading speed – regardless of where your site is viewed. We strongly recommend that you use a CDN for website performance. Our preferred CDN is Amazon Cloudfront. It is economical and provides excellent service. You must first setup an account on Amazon S3 where your content will actually be stored. Establish your ‘bucket’ on S3 then upload your content into the bucket. You then create a distribution on your Cloudfront account which will have an associated domain name. The domain name is used to load your images and videos on your web page. Once your Cloudfront distribution is ‘deployed’ it is available to the viewers of your website. Contact us for more information on how to use a Content Delivery Network and to discuss your options.
A content delivery networks provide rapid content delivery across a large geographical area. Using a CDN for images and videos will significant improve page loading speed – regardless of where your site is viewed. We strongly recommend that you use a CDN for website performance. Our preferred CDN is Amazon Cloudfront. It is economical and provides excellent service. You must first setup an account on Amazon S3 where your content will actually be stored. Establish your ‘bucket’ on S3 then upload your content into the bucket. You then create a distribution on your Cloudfront account which will have an associated domain name. The domain name is used to load your images and videos on your web page. Once your Cloudfront distribution is ‘deployed’ it is available to the viewers of your website. Contact us for more information on how to use a Content Delivery Network and to discuss your options.
Category Archives: Uncategorized
Critical Java Update
 If you are running Java (more on that in a moment), you must install the latest update:
If you are running Java (more on that in a moment), you must install the latest update:
Oracle informs us that at least four of the 37 security holes plugged in this release earned a Common Vulnerability Scoring System (CVSS) rating of 10.0 — the most severe possible. Vulnerabilities with a 10.0 CVSS score are those which can be easily exploited remotely and without authentication, and which result in the complete compromise of the host operating system.
But before you update your Java installation, first ask yourself if you really need Java. The safest way to use Java is to uninstall it altogether. It’s a security nightmare. So, why do you need Java? There are some programs that require Java. LibreOffice, for example, requires Java. Online chat, some games… the question is, can you live without it? We recommend that you uninstall Java from your computer and see what difference it makes. If something stops working, find an alternative program.
To uninstall Java, go to your control panel and select Add/Remove Programs. Find ALL occurrences of Java (Java didn’t uinstall previous versions until recently and those early Java installations are very dangerous) and uninstall them. If you are running a Mac, your Java has already been disabled or was not installed – unless you are on OSX version 10.6 or earlier in which case removing Java can actually damage your system. Consult your Apple Expert for assistance.
But if you decide that you must have Java, get your Java update now and install it… if you are running Java. Once you have installed the most recent update, you will want to disable Java in your browser(s). To do this first close any browsers that are open. Go to Start>>Computer and type “Javacpl.exe” in your search bar. If you find it, double-click on it to run it. Some computers, however, will not find it tis way. Instead you’ll need to find it manually. Go to Start>>Computer>>Local Disk (C:). If you have a 64-bit computer, go to Program Files (x86)>>Java>>jre7>>bin. On 32-bit computers, you’ll find it in Program Files>>Java>>jre7>>bin.
Double-click Javacpl.exe and find the Security tab. Uncheck the box that says “Enable Java content in the browser.” Now your browsers will not use Java which will render you much safer on the dangerous universe we call the internet.
Major News That Could Affect You
There were two major news items reported today with potential for affecting you.
First, 450,000 Yahoo accounts were hacked today. If you have a Yahoo account, you need to change your password now. If you use that same password anywhere else, you need to change those passwords as well. While you’re doing that, make sure you’re using proper password management. DO NOT use the same password everywhere. Your most sensitive accounts – banking and other financial records for example – should not share a password with any other account. You should be using a password manager program that offers secure storage and the ability to safe backup all your passwords. You can read more about these and other personal security measures on this blog post.:
 Second, the sun emitted a huge flare today. Granted, no electronic damage is expected from today’s flare, but there may be a flare in the future – perhaps the not-so-distant future – that will wipe out your computer. Are you properly backed up? See the blog post referenced above for more information.
Second, the sun emitted a huge flare today. Granted, no electronic damage is expected from today’s flare, but there may be a flare in the future – perhaps the not-so-distant future – that will wipe out your computer. Are you properly backed up? See the blog post referenced above for more information.
Hiring a Web Developer Part 03
Writing the Request for Proposal (RFP) Document
 First, what is an RFP and why should you write one? An RFP represents an essential element in selecting and working with a website developer. Initially, the process of writing an RFP helps you define exactly what your website must do, how it must appear, and how it must function. It assists you in coming to a thorough understanding of exactly what your website project looks like. Even if you did nothing else with the RFP, this alone justifies the time and effort of developing an RFP. It also pulls all the members of your internal team together, unifying your vision of your new website. Primarily, it is the instrument of communication between you and your website developer, whoever that turns out to be. This is critical, because the developer will bid upon this understanding – anything that must be added or changed through the project will cost your company money! Finally, it is the means by which you will compare the companies bidding on the project. So this RFP document is very valuable indeed – and it must be properly designed before it is ever sent to a developer.
First, what is an RFP and why should you write one? An RFP represents an essential element in selecting and working with a website developer. Initially, the process of writing an RFP helps you define exactly what your website must do, how it must appear, and how it must function. It assists you in coming to a thorough understanding of exactly what your website project looks like. Even if you did nothing else with the RFP, this alone justifies the time and effort of developing an RFP. It also pulls all the members of your internal team together, unifying your vision of your new website. Primarily, it is the instrument of communication between you and your website developer, whoever that turns out to be. This is critical, because the developer will bid upon this understanding – anything that must be added or changed through the project will cost your company money! Finally, it is the means by which you will compare the companies bidding on the project. So this RFP document is very valuable indeed – and it must be properly designed before it is ever sent to a developer.
We have provided a template (click on the document image at left to access the template) but please understand that there is no one design for an RFP. The RFP must reflect your project thoroughly, so you will probably need to make some revisions to the template. The template offers a starting point.
The most important part of the document is the Functional Requirements section. Your prospective web developers will base their estimate primarily on the information contained within this section. Review this section carefully with all members of your internal team to ensure that it is complete and accurate.
Once the proposal documents have been returned, carefully evaluate each one, looking to ensure that they address each issue of the RFP document. The proposals will provide a good indication as to which web designers you should interview in the next stage of the process.
Handling Blog Comments
You will notice that few comments appear on my blog. It’s not that I haven’t received comments – I receive several comments every day, especially on the Typography blog post – but the vast majority of the comments do not contribute to the blog. Unless the comment offers something of value to the readers of the blog, I don’t approve it. Typically these comments are something along the lines of “Thank you for your blog posting. It’s a very nice blog.” Certainly a nice sentiment, but it doesn’t offer any value. They are almost always from someone at a company trying to promote their own website by having links to their website on someone else’s blog. It is important to have links on other websites and offering comments on other people’s blog is a good way to do that – but there must be valuable content in the comment to make it worthy of reading and following the link back to your site. Otherwise, it’s a waste of time.
A useful comment would be something along the lines of, “I have received a great deal of positive feedback on my website by using the techniques recommended in this blog. My website’s typography looks much more professional and refined and my readers have commented that it make it easier to read. Another great resource I’ve found for typography is (website address.)” This is a comment I would approve. Even a negative comment such as, “I disagree. I think it’s ridiculous to spend that much time just making the typography look pretty – the readers come to my website for information, no to ooh and ah over a pretty website.” At least it’s an expression of opinion that is relevant to the topic and will, hopefully, generate more discussion.
Comments are resources for your blog. If the writer of the comment has typos or grammar errors, correct them before approving the post. Their errors would reflect badly on your own blog. Of course, you do not allow comments to appear on your blog until they have been reviewed – it is much too dangerous to allow people to add content to your website without your approval.
Blogs collect a lot of spam. There are filters such as Akismet (no longer free except for personal websites) or Mollom that help reduce it, but it is just a fact of life that blogging will include processing spam. Even if Akismet or Mollom don’t consider a comment to be spam, does it add value to your blog? You still have to do some manual filtering, though it will be much less than without the filter.
Typography and Web-Safe Fonts
Typography represents one of the great challenges in building an engaging and dynamic website. The greatest challenge lies in the fact that there are very few fonts a web designer can use that will be properly presented to all users. Fonts will only be properly displayed if they are installed on the user’s computer. If the designer opts for a beautiful font but the font is not installed on the user’s computer, the computer makes its own decision on what font should be used in the place of the specified font which may provide extremely disappointing results.
In this case, the design can – and definitely should – provide a list of fonts to use in decreasing order of desirability. This greatly enhances the possibility that the page will be rendered in an acceptable fashion, especially if one or more of the so-called web-safe fonts are included in the list. These are fonts that exist on the vast majority of computers – the nearly universal fonts such as arial, verdana, courier, and georgia. These fonts exist in one of just a few variations on pretty much every computer available, although the names may change between various operating systems.
There are work-arounds. Google fonts provide a much larger list of fonts available, but the fonts typically look a little odd. They’re just not presented well. In addition, there are some other services that will allow you to use fonts hosted on their servers. Most of these charge for that service. I can’t honestly speak to the quality of presentation because I haven’t tried them. Extensis and Font Agent Pro are the two dominant players in the field. If you have experience with these or similar services, please leave a comment, describing your experience with them.
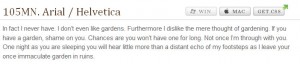 Virtual Websource prefers to use the websafe fonts in more imaginative ways. By playing with the spacing, sizing, and other characteristics of the 15 or so web-safe fonts, a wide range of typographic presentations may be generated. An excellent resource for viewing and obtaining the style sheet control codes to generate those results may be viewed at TypeChart.com. Go view their displays and be prepared to be impressed.
Virtual Websource prefers to use the websafe fonts in more imaginative ways. By playing with the spacing, sizing, and other characteristics of the 15 or so web-safe fonts, a wide range of typographic presentations may be generated. An excellent resource for viewing and obtaining the style sheet control codes to generate those results may be viewed at TypeChart.com. Go view their displays and be prepared to be impressed.
For assistance in improving your website’s typography, Contact Us.